This is an updated version of a story first publised on Feb. 1.
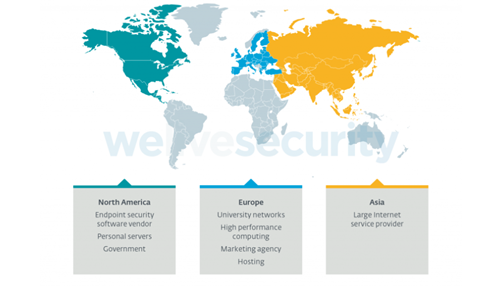
Kobalos attack targets — North America: Endpoint security software vendor, Personal servers, Government; Europe: University networks, High performance computing, Marketing agency, Hosting; Asia: Large internet service provider
UK technology industry publication PCR published a story today stating that an international data security firm, ESET, has reported the identification of a malware called Kobalos that targets supercomputing clusters. They also said they have been working with security experts at CERN, the European Organization for Nuclear Research and other organizations on stemming attacks.
“Among other targets was a large Asian ISP, a North American endpoint security vendor as well as several privately held servers,” PCR reported.
ESET issued a press statement and a white paper today offering detailed findings about the malware. The firm said staff members reverse engineered what the firm described as a “small, yet complex malware that is portable to many operating systems, including Linux, BSD, Solaris, and possibly AIX and Windows,” PCR reported.
ESET Senior Malware Researcher Marc-Etienne Léveillé told PCR the malware has been named Kobalos “for its tiny code size and many tricks; in Greek mythology, a kobalos is a small, mischievous creature. It has to be said that this level of sophistication is only rarely seen in Linux malware.”
The story said Kobalos includes broad commands that conceal the intent of the attackers.

“In short, Kobalos grants remote access to the file system, provides the ability to spawn terminal sessions, and allows proxying connections to other Kobalos-infected servers,” said Léveillé.
After a server has been successfully penetrated by Kobalos, the hardware can be turned into a command & control server by the operators sending a single command,” PCR reported. “As the C&C server IP addresses and ports are hardcoded into the executable, the operators can then generate new Kobalos samples that use this new C&C server. In addition, in most systems compromised by Kobalos, the client for secure communication (SSH) is compromised to steal credentials.”
“Anyone using the SSH client of a compromised machine will have their credentials captured,” Léveillé told PCR. “Those credentials can then be used by the attackers to install Kobalos on the newly discovered server later.”

Marc-Etienne-M.Leveille
To reduce the Kobalos threat, ESET suggested implementing a two-factor authentication for connecting to SSH servers because “stolen credentials seems to be one of the ways it is able to propagate to different systems.”
In a statement released today (Feb. 2), ESET stated that “perhaps unrelated to the events involving Kobalos, there were multiple security incidents involving HPC clusters in the past year. Some of them hit the press and details were made public in an advisory from the European Grid Infrastructure (EGI) CSIRT about cases where cryptocurrency miners were deployed. The EGI CSIRT advisory shows compromised servers in Poland, Canada and China were used in these attacks. Press articles also mention Archer, a breached UK-based supercomputer where SSH credentials were stolen, but does not contain details about which malware was used, if any.”



